Knowing where to look and what to look for is critical in the successful detection and investigation of phishing attacks.
The wide adoption of digital technologies has introduced a significant productivity boost to enterprises and individuals. Nowadays, most people and business interactions happen in what is known as cyberspace or the internet.
Criminals know this and are moving their criminal operations from the real -physical- world into cyberspace. Companies are aware and continually invest in deploying the latest technological solutions to prevent cyber attacks against their computerized systems. Still, the number of cyber attacks and their financial loss are continually increasing.
According to Cyber Security Venture, global cybercrime costs will reach $10.5 trillion annually by 2025. To mitigate the ever growing cost of cyber attacks, organizations are deploying various types of security solutions to win the race against cybercriminals. However, despite these deployments, threat actors can still infiltrate the most protected networks by exploiting the human element. These types of attacks are referred to as social engineering (SE) attacks, and this guide covers the most prominent type, phishing.
What is a phishing attack?
The phishing attack is a type of SE attack that can be executed via:
- Websites
- Internet messaging applications – such as WhatsApp and Google Chat, in addition to social media messaging services, such as X direct messages and Facebook Messenger
- Phone calls
- SMS messages
- In-person
As with all SE attacks, phishers aim to deceive unaware internet users into revealing sensitive information, such as:
- Account login credentials
- Personal identifiable information (PII), including social security numbers and medical records
- Credit card and banking information
Phisers will also deceive their victim into installing malware on the victim's computing device to execute various malicious actions – such as installing ransomware or keyloggers to infect user devices and consequently spread the infections to other corporate devices.
Executed through phishing, wire transfer fraud also aims to convince a target to transfer money to an account controlled by the attacker.
Phishers communicate with their victims by impersonating a trusted source, such as a user:
- Financial institutions: like banks, online money companies like PayPal and credit cards companies. Attackers aim to steal the target user's banking information to steal their money.
- E-commerce websites: such as Amazon and eBay. The aim here is to steal both users' personal and financial information.
- Social media platforms: such as Facebook, Instagram or X. In this type, the attackers aim to steal user access credentials and other personal information to execute further attacks and conduct fraud operations.
- Professional networks: such as LinkedIn. Some attackers impersonate professional network agents and offer fake job opportunities to unsuspecting users. The aim here is to promise users that they will find a job and request fees in addition to stealing their personal information.
Phishers may target a specific person or send their phishing emails and SMS messages to a large audience. When targeting a particular person, threat actors need to collect various information about them before initiating the communication. In that case, attackers leverage open-source intelligence (OSINT) to gather as much information as they can about their target from publicly available sources.
Common phishing attack techniques
Phishing attacks can take a variety of forms. Here are the most common ones:
Email phishing
This is the most common form of phishing attacks. In this type, threat actors send fraudulent emails disguised as legitimate messages from trusted entities (companies or individuals). These emails commonly contain malicious links or attachments that, when clicked, can install malware or drive the unsuspecting user to visit a malicious website housing an exploit kit to steal their sensitive information.
Phishers use different tactics to conceal the actual destination of the URLs contained in their email, such as:
- Using shortened service such as Bitly and ShortURL
- Using display text that is different from the link. For example, “Click here to verify your [bank] account”. When you hover your mouse over the link, it will display a link that does not point to the bank (see Figure 1).
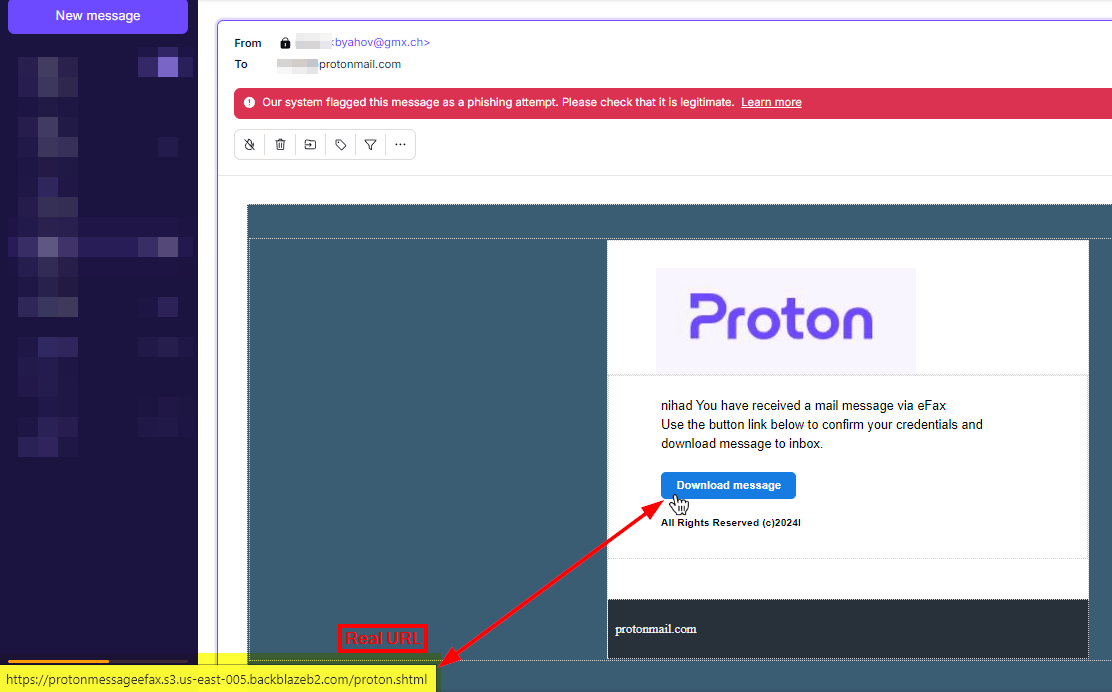
Figure 1 - Hover over the link in the suspicious email to reveal the actual URL destination.
- Using the typosquatting technique. Attackers register domain names whose names are very close to the legitimate websites. For example, www.authentc8.com (the “i” is omitted from the name) instead of www.authentic8.com
- Using embedded images that point to the attacker's website. It is common for phishers to use images within emails to link to their website. The embed image may contain a legitimate logo of the business they are impersonating while it points to the phisher's website.
Website forgery
Phishers create fake websites that closely resemble legitimate sites, such as banking portals, social media platforms, or online merchant sites. Then, unaware users are tricked into entering their login credentials or personal information on these fake sites using different SE tactics.
It is common for attackers to get a cloned version of the target web pages they want to impersonate. For example, attackers use website downloaders to get a cloned version of the target website, then upload this version to their hosting space after connecting the site login and registration forms to their servers to store stolen user information.
Here are some free website downloader tools:
Spear phishing
Spear phishing is a more targeted version of email phishing. While ordinary email phishing is sent in bulk (for thousands or even millions of recipients at the same time), spear phishing targets specific individuals after collecting some information about their backgrounds to craft customized emails or conversations.
Threat actors commonly leverage OSINT tactics to gather intelligence about spear phishing targets before executing the attack. Here are some techniques attackers use to collect such information:
- Purchase information from other hackers, commonly from darknet marketplaces such as the TOR network. Some websites on the dark web even sell hacking services for a fee (see Figure 2).
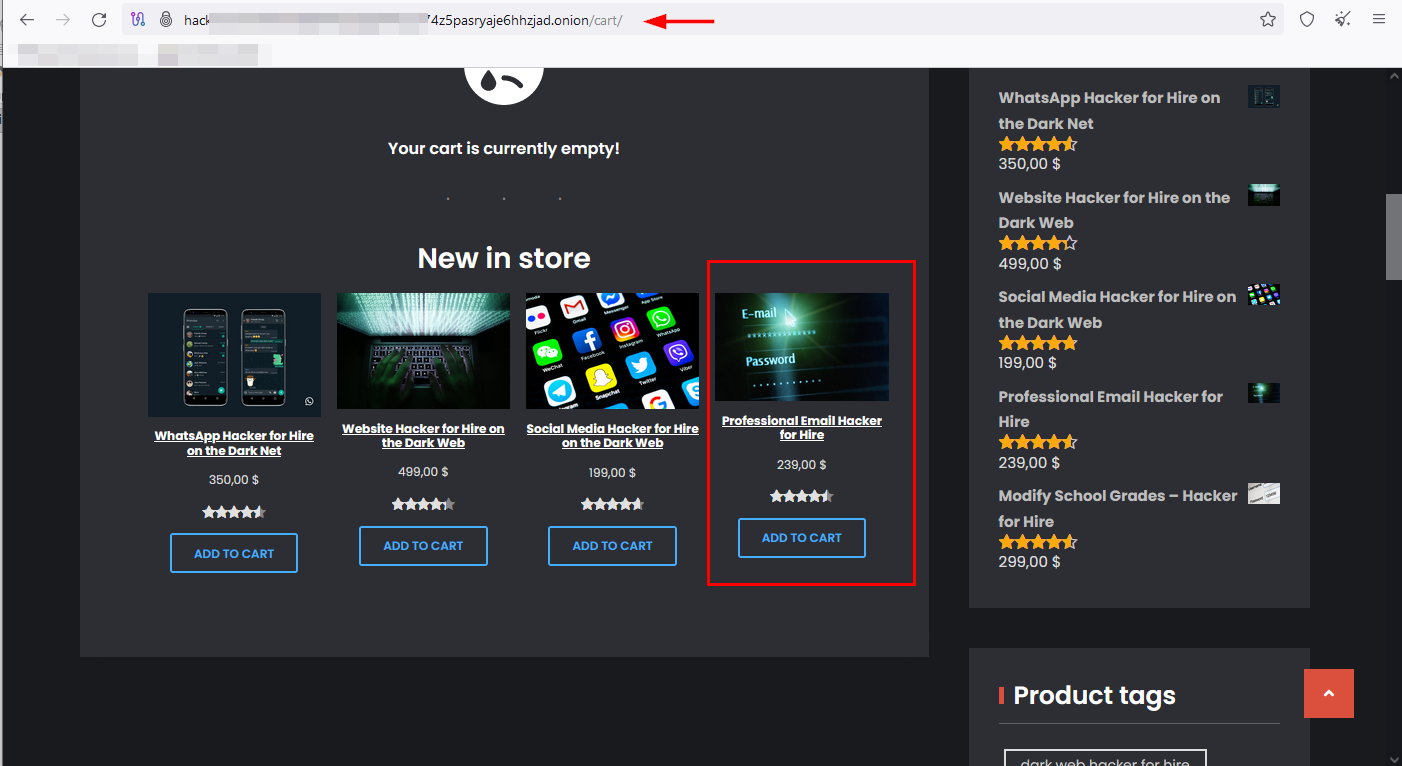
Figure 2 - Some darknet websites promote hacking services to infiltrate any email account for a fee
- Malware infection: Cybercriminals may try installing malware on different users' devices to steal their information – such as stealing legitimate email account credentials. This way, they can send phishing emails from compromised email accounts, making the spear phishing attempts look more trustworthy when the target receives them.
- Social Engineering (SE) techniques: Phishers may use different SE tactics to gather information about a particular user. For example, they can seek information on a specific target by interacting with the target's friends on social media platforms, pretending to be someone they know or can trust.
- Credential stuffing: Attackers may utilize previously breached accounts to obtain information about future victims. Different online repositories list previously breached account credentials, which the attackers can use to gain unauthorized access to other accounts where users are using the same credentials. The most popular one is Have I Been Pwned.
- Compromised websites: Phishers can collect email addresses from compromised websites by injecting malicious code into them. When unaware users visit these websites, the malicious code can extract email addresses — and even saved account passwords — from their computers by exploiting potential vulnerabilities in their operating system and/or installed applications.
Go even deeper on how to investigate phishing sites >
Vishing
This type uses phone calls and audio messages to impersonate a legitimate entity. Hackers use different SE tactics to convince their targets to reveal sensitive information or even instruct them to install malware on their devices. Consider a scenario where a hacker pretends to be a customer support agent from your bank and asks you to install a banking application on your smartphone or computer (for easy access to your online banking account) that secretly contains a keylogger or other malware.
Pharming
Pharming is a more advanced form of phishing. It requires technical knowledge from the attackers because it works by manipulating the target website's DNS servers or the victims' HOST file to redirect them to the attacker's website. This hijacking of the DNS resolution process is why this attack is sometimes called a DNS spoofing attack.
By poisoning DNS servers or modifying the HOST file on the victim's computing device, pharming attacks will redirect unaware users to the attackers' websites even when they type the correct URL into their browser.
Angler phishing
Angler phishing leverages social media platforms to communicate with its victims. The attack scenario works as follows:
Hackers create a fake social media account (for example, on Facebook or X) that impersonates a legitimate business or brand. Afterward, hackers search for customers complaining about the company's impersonated product or service. For instance, a customer may have used the repair service of a mobile phone shop and is complaining online about the bad service – such as posting negative opinions about their service. Attackers try to communicate with this customer from their fake profiles and attempt to conduct malicious actions – such as stealing personal information, asking for money to repeat the repair, or simply asking them to install a customer support app (which contains a keylogger) to steal users' sensitive information.
With social engineering attacks on the rise, it is necessary to be aware of the most prominent types of phishing attacks. Knowing what to look for is key in detecting and investigating these types of attacks to ensure you and your organization remain vigilant and safe in today’s complex cyber threat landscape.
Investigate phishing attacks safely with Silo for Research
When SOC analysts are alerted to a potential phishing attack, they need a secure (isolated) and anonymous environment to investigate the web content in question. Watch the demo above to see how Silo for Research:
- Empowers analysts to "blend in with the crowd" by manipulating their internet egress location and corresponding details (language, time zone, keyboard settings, etc.)
- Improve efficiency by automating multi-search workflows
- Easily capture content with URL and timestamps
- Save collected information to secure cloud storage and seamlessly share for collaboration
Discover all that Silo for Research can do for your SOC team and start a 30-day free trial today!


